Google wants to make Chrome Extensions more secure
Google announced a number of changes to Google Chrome's extensions system designed to make the use of extensions more secure.
The company has been in a constant battle against misuse of extensions that are either outright malicious or problematic from a privacy perspective.
Yesterday's announcement is the next step to make extension use securer. I reviewed the option to limit extensions with unlimited access to site data yesterday already. Chrome users may set extensions to "click to activate" or to a subset of sites they activate automatically starting with Chrome 70.
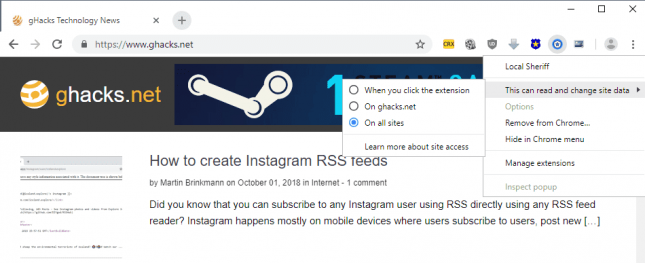
Extension developers face a number of changes as well. Extensions that use obfuscated code are no longer allowed on the Store. Existing extensions that use code obfuscation have a grace period of 90 days while new extensions can't have any obfuscated code as they will be denied otherwise.
Google revealed that over 70% of malicious and policy violating extensions make use of code obfuscation, often to avoid detection by the Store's automatic scans to detect malicious or problematic extensions.
The change does not affect minification efforts to reduce the size of code. Minification techniques that are still allowed include removal of whitespace or code comments, or the shortening of variables and functions.
Existing extensions that are offered in Store at the time have 90 days to upload extension code that is not obfuscated. Extensions that fail to meet the deadline will be removed from the Chrome Web Store as a consequence.
Another change that affects extension developers directly is that developers need to enable 2-step verification for developer accounts in 2019.
Criminals have tried (and succeeded) in gaining access to developer accounts in the past to hijack accounts and push out extension updates that introduce malicious or problematic code
The third and final change affects the review process. Chrome extensions are reviewed automatically when a developer submits them. While automation is cost-efficient, it does not offer 100% protection against malicious extensions as the past has shown.
Extensions "that request powerful permissions" will have to pass "additional compliance" reviews and extensions that "use remotely hosted code" will be monitored closely.
Google plans to release an updated Manifest for extensions in 2019 "to create stronger security, privacy, and performance guarantees". Key goals include giving users additional mechanisms to control extension permissions, APIs that are "more narrowly-scoped", and introduction of new capabilities.
Closing Words
Google is finally doing something about malware and problematic extensions in the Chrome Web Store. Banning extensions with obfuscated code is a welcome step and so is the additional monitoring and review steps for some extensions.
My personal favorite is the ability to restrict where extensions can run that are designed to run on all pages.
Now You: Do you think the changes are enough to make the Chrome Web Store cleaner?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments