GNU/Linux Security: A look at QubesOS
Using GNU/Linux is by default more secure than using Microsoft Windows, this is common knowledge; however just because you use GNU/Linux, does not mean that your system is secure, and that is why some distributions have been created in order to maximize security; such as QubesOS.
QubesOS is very different from your typical run of the mill distro, such as Ubuntu or even the more hardcore like Arch Linux and Gentoo. QubesOS runs multiple virtual machines linked together under a single user-interface, to form a container based / compartmentalized operating system.
The purpose of this, is hypothetically speaking if an adversary were to gain remote access into your machine, they would be bound to only having access to the compartment they broke into.
To give a real example: Let's say that you have two 'compartments' running, and you visit a website with malicious code injected into it with your Firefox browser from compartment1, all your banking information, photos of your children, and that surprise anniversary gift ideas text document list you've been working on for your wife; is hypothetically safe from those prying eyes, tucked away in compartment2.
QubesOS
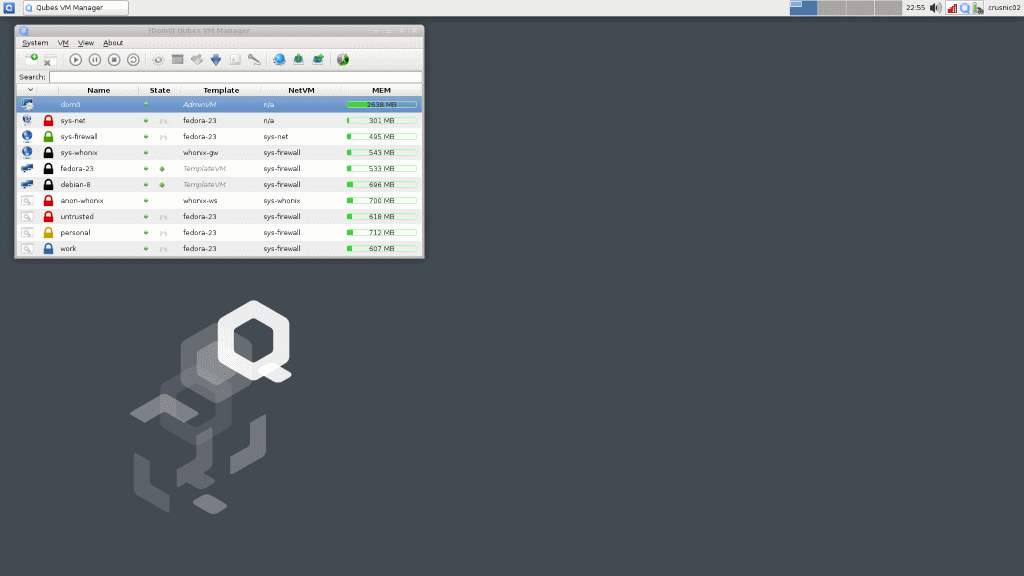
QubesOS utilizes three different distributions simultaneously, Debian, Fedora, and one that some of you may not have knowledge of; Whonix.
Whonix is a GNU/Linux distribution that routes all Internet traffic through the TOR network for the purpose of privacy and anonymity.
The machine I used for this has the following specs:
- Intel Core i5-4210U
- 8GB DDR3
- SSD
- Running QubesOS installed to it's own partition, NOT LiveUSB or in a VM.
The Installation
I was unable to snap screenshots of the installation, so you will have to trust in my word that the installation of QubesOS was surprisingly straightforward and very easy to figure out. Granted, I've installed countless distributions in my life using both graphical environments and command line interfaces alike, but I would say that unless QubesOS is your first delve into the GNU/Linux world which I DO NOT RECOMMEND, you should be able to manage.
The installer gave the option for automatic installation as well as manual partitioning (which was what I opted to do), and was no different than setting up any other GNU/Linux operating system.
Something that is obvious for a distribution like this to include, but that I thought was worth mentioning, was that by default QubesOS opts to use DM-LUKS full disc encryption for the installation, meaning that your entire setup (minus the /boot partition) is encrypted; something I support highly and tend to do with my installs on any system anyways.
The installation did take considerably longer than most do, but given the complexity of the operating system, it was no surprise to me really; taking around 30-45 minutes before it was fully finished and I was able to reboot into the system.
Note: QubesOS is NOT recommended for Dual-Boot situations. Although it's possible, it does leave security holes, and therefore the QubesOS team does not recommend it.
Working within QubesOS
QubesOS when I first booted in, greeted me with a standard encryption lock screen with the Q logo. Nothing fancy, but no need for there to be really. After that I was taken to a post-installation setup screen where I was asked to check/uncheck boxes about how I wanted QubesOS to handle certain things such as USB devices.
I checked that I wanted them to be handled by a system called usb-sys; as I wanted to make sure that I was protected against physical attacks using USB devices, not just attacks from external sources; I do a large number of server related tasks, my personal banking, my Ghacks articles and my schoolwork all from one singular laptop, I'd rather have more security than less.
Once that was done, I was able to exit that screen and was then taken to the LightDM-GTK login screen (the typical Xfce login screen). Entering my password took me to my default desktop.
QubesOS uses Xfce as its Desktop Environment, and it suits it well, looking very professional and no frills, but pretty enough to look 'modern' if you will. The only thing I had on my screen by default besides my top panel, was what's called the “Qubes VM Manager,” which you can see in the screenshot above. This VM Manager, shows all the core details for all of the various virtual machines running, like memory usage. This is where you'll refer to if you need to reboot a VM for any reason, or which to make new ones.
During the installation, I opted to use the default VM setup, so I have quite a number of VM's running, however you might (and I might if I decide to use QubesOS long term) want to select less / customize your own for your own purposes.
The defaults are
- Disposable VM – A complete throwaway, where once the software you run is shut down, the VM is also destroyed until you make a new one.
- Anon-Whonix – A Whonix VM where all traffic is routed through the TOR network.
- Personal – Used for your own personal files and activities.
- Untrusted – Probably the VM you should be using anytime you aren't visiting a trusted website or downloading totally trusted files. This is where I'd imagine a user will do most of their web browsing.
- Vault – Probably where you want to be running applications or downloading files you definitely want to keep safe. Going to do online banking? Storing photos of your family? Do it here.
- Work – Self explanatory.
Now, some explanation is needed. Something to point out to you is that if you download a photo of a dog while using your web browser from the 'Personal' Qube, and then you enter your file manager from your 'Work' Qube, you will not find that dog photo.
It's a separate VM, you could almost think of it like having multiple computers themselves, all in your one screen. However, thankfully, you can transfer files between Qubes very easily by right clicking the files you want, and selecting either “Move to other AppVM” or “Copy to other AppVM” and then entering the name of the Qube you wish to transfer the file to, such as “Vault” or “Work.”
Another thing to point out, is that on top of these “Domains” they are called by QubesOS, there are also menu items for “Templates.”
The above Qubes, are all created from “Templates” of distribution such as Fedora, Debian or Whonix. All of mine were based off of Fedora or Whonix, although I did have a Debian-8 Jesse template as well. You do not install software into your “Domains”, but rather into the “Templates” in QubesOS, and then the software becomes available into the “Domains.” A little confusing at first, but it became relatively straight forward fairly quickly as I messed around with it.
There is more to it, but this is the basis of QubesOS and how it functions. This overview is not meant as a full tutorial. If you have installed QubesOS and need documentation on how to do something, more information can be found on the QubesOS doc page.
Applications
QubesOS does come with the usual software, music players, photo management, file manager, Firefox web browser etc. However, I did note that it did not come with LibreOffice for example, and I had to install that myself.
By default, with the setup that I have described, all of my main VM's (Personal, Work etc) are using the Fedora Template system, and so in order to install LibreOffice, I had to go into my panel menu, access the Fedora-23 template, and install LibreOffice, and then restart the VM, and the associated VM's as well using the VM Manager. After that, I had LibreOffice available to me, and began working on this article.
It took me a little while to get used to the whole 'everything is compartmentalized and not accessible between Qubes by default' way of doing things, but after a few hours of installing things, poking and prodding around, I got the hang of it.
One thing on the topic of applications to point out, is that 3D gaming will not be happening on QubesOS, because OpenGL opens up many potential avenues for threats, as well as would need to have the QubesOS team drastically alter many aspects of the OS. So, if you're a gamer, QubesOS is not for you.
Final Thoughts
QubesOS is pretty advanced. I wouldn't recommend it if you're not quite comfortable and knowledgeable with GNU/Linux, package managers, and if you are not ready to give up the traditional way of looking at your Operating System. However, if you are serious about security, and you want to take the next step, QubesOS is a great way to do things.