Firefox 52.0 released: find out what is new
Mozilla Firefox 52.0 Stable was released on March 7, 2017 to the public through the web browser's automatic update functionality, and on Mozilla's website.
Note: Firefox 52.0 is being rolled out on March 7, 2017. The release is already on Mozilla's FTP server, but may not be yet available through automatic updating. All Firefox users and interested Internet users will have access to the release at the end of the day.
The new version of Firefox is a major release for several reasons. First, it is the first release that does away with NPAPI plugin support. Second, it marks the beginning of a new Firefox Extended Support Release (ESR) cycle.
Mozilla updates all Firefox channels on the same day when a new major stable version is released. This means that Firefox Beta is updated to Beta 53.0, Firefox Aurora to Aurora 54.0, and Firefox Nightly to Nightly 55.0. Additionally, Firefox ESR 52.0 is available (and so is Firefox ESR 45.8).
Executive Summary
- Firefox 52.0 is the new stable version of the web browser.
- The new version does not support NPAPI plugins anymore, apart from Adobe Flash. So, no Silverlight, Java, Google Hangouts and other plugin support anymore.
- Firefox ESR 52.0 is the new Extended Support Release version. You may enable NPAPI plugin support in it.
- Windows XP and Vista users are automatically migrated to Firefox 52.0 ESR during update. Firefox 53.0 won't run on XP or Vista machines anymore.
Firefox 52.0 download and update

Mozilla Firefox 52.0 is available on Mozilla's public FTP server. The update will be made available today through the browser's automatic update feature, and also on the Mozilla website.
You can run manual check for updates in the following way in Firefox:
- Open Firefox if it is not open already.
- Tap on the Alt-key on your computer keybard, and select Help > About Firefox.
This displays the current version and channel of the browser. An update check is performed in the background, and new versions that are found during the check are either downloaded and installed automatically, or on user request.
The latest Firefox versions can be downloaded by following the links below as well:
- Firefox Stable download
- Firefox Beta download
- Firefox Developer download
- Nightly download
- Firefox ESR download
- Firefox unbranded builds information
Firefox 52.0 Changes
Non-Secure warnings for HTTP login pages
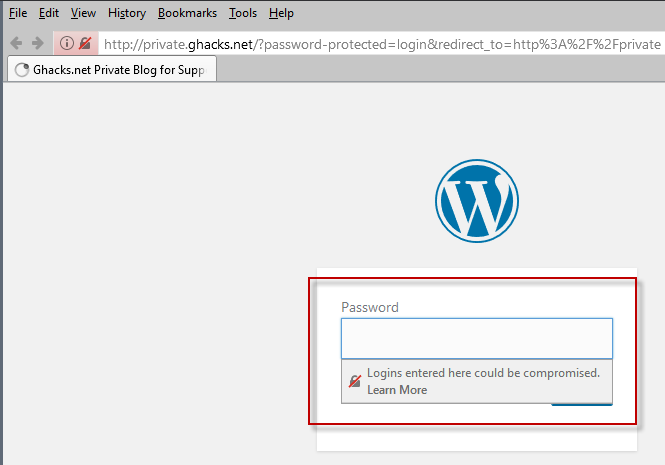
Firefox warns you with a security prompt when a page with a login form uses HTTP. The browser displays a small notification underneath the login prompt when you activate it if HTTP is used on the page to submit the data.
Also, autofill disabled on these pages.
It reads: Logins entered here could be compromised. Learn more.
Strict Secure Cookies specification implemented
The Strict Secure Cookies specification has been implemented. It prevents insecure (read HTTP) sites from setting cookies with the secure flag. It prevents HTTP sites from overwriting cookies set by HTTPS sites with the secure flag.
You find the draft here.
Firefox 52.0 ESR
Firefox 52.0 ESR marks the beginning of a new extended support release cycle. This release is important for a number of reasons:
- It is the only version of Firefox going forward that supports NPAPI plugins other than Adobe Flash. To enable support for other plugins, set plugin.load_flash_only to false on about:config.
- It is the last version of Firefox going forward that supports Windows XP and Windows Vista. While Firefox 52.0 will install fine on machines running those operating systems, Firefox 53.0 will fail to run.
- You may still disable the signature enforcement for add-on installations. Set xpinstall.signatures.required to false for that.
- Service Workers, Push Notifications, and WebAssembly not enabled by default. To enable, set dom.serviceWorkers.enabled, dom.serviceWorkers.openWindow.enabled, dom.push.enabled and javascript.options.wasm to true.
Other Firefox 52.0 changes
- Added support for WebAssembly.
- Added automatic captive portal detection which should improve access to WiFi hotspots. "When accessing the Internet via a captive portal, Firefox will alert users and open the portal login page in a new tab".
- Adobe Primetime CDM is removed.
- A warning is displayed when when SHA-1 certificates are encountered that chain up a root certificate. Users may still override the warning.
- Improved text input for third-party keyboards on Windows. According to Mozilla, this fixes several keyboard issues such as chained dead keys and dead key sequences.
- Multi-process Firefox is now available on Windows systems with touch screens.
- Option to expose only whitelisted fonts to websites and services.
- Removed support for the Battery Status API for privacy.
- Sync enables Firefox users to send and open tabs from one device to another.
- When Direct2D is not used on Windows, Skia is used instead for content rendering.
Developer Changes
- The Responsive Design Mode of the Developer Tools has been revamped completely.
- CSS Grids highlighter in the Page Inspector module.
- New CSS features implemented. See developer notes linked at the bottom for details.
- New JavaScript features: async functions, trailing commas in functions, rest parameter destructuring, and more.
- Page Inspector: easier element highlighting, and display of whitespace-only text nodes.
- Referrer-Policy supports same-origin, strict-origin, and strict-origin-when-cross-origin directives.
- Rel="noopener" link type has been implemented.
- Selection API shipped.
- Service Worker State shown on about:debugging now.
- Several Firefox OS APIs removed.
- WebExtensions APIs: sessions, topSites, omnibox shipped.
Firefox 52.0 for Android
Many features that landed in Firefox on the desktop landed in Firefox for Android as well. The following changes are Android specific.
- The apk file size of the Firefox browser has been reduced by more than 5 Megabyte. This should improve download speed and installation time.
- Media controls are displayed in the Android notification area to pause and resume media playback.
Security updates / fixes
Mozilla reveals security updates after the final release. We will update the listing with information once Mozilla publishes it.
- CVE-2017-5400: asm.js JIT-spray bypass of ASLR and DEP
- CVE-2017-5401: Memory Corruption when handling ErrorResult
- CVE-2017-5402: Use-after-free working with events in FontFace objects
- CVE-2017-5403: Use-after-free using addRange to add range to an incorrect root object
- CVE-2017-5404: Use-after-free working with ranges in selections
- CVE-2017-5406: Segmentation fault in Skia with canvas operations
- CVE-2017-5407: Pixel and history stealing via floating-point timing side channel with SVG filters
- CVE-2017-5410: Memory corruption during JavaScript garbage collection incremental sweeping
- CVE-2017-5411: Use-after-free in Buffer Storage in libGLES
- CVE-2017-5409: File deletion via callback parameter in Mozilla Windows Updater and Maintenance Service
- CVE-2017-5408: Cross-origin reading of video captions in violation of CORS
- CVE-2017-5412: Buffer overflow read in SVG filters
- CVE-2017-5413: Segmentation fault during bidirectional operations
- CVE-2017-5414: File picker can choose incorrect default directory
- CVE-2017-5415: Addressbar spoofing through blob URL
- CVE-2017-5416: Null dereference crash in HttpChannel
- CVE-2017-5417: Addressbar spoofing by draging and dropping URLs
- CVE-2017-5425: Overly permissive Gecko Media Plugin sandbox regular expression access
- CVE-2017-5426: Gecko Media Plugin sandbox is not started if seccomp-bpf filter is running
- CVE-2017-5427: Non-existent chrome.manifest file loaded during startup
- CVE-2017-5418: Out of bounds read when parsing HTTP digest authorization responses
- CVE-2017-5419: Repeated authentication prompts lead to DOS attack
- CVE-2017-5420: Javascript: URLs can obfuscate addressbar location
- CVE-2017-5405: FTP response codes can cause use of uninitialized values for ports
- CVE-2017-5421: Print preview spoofing
- CVE-2017-5422: DOS attack by using view-source: protocol repeatedly in one hyperlink
- CVE-2017-5399: Memory safety bugs fixed in Firefox 52
- CVE-2017-5398: Memory safety bugs fixed in Firefox 52 and Firefox ESR 45.8
Firefox ESR 45.8 security fixes are here.
Additional information / sources
- Firefox 52 release notes
- Firefox 52 Android release notes
- Add-on compatibility for Firefox 52
- Firefox 52 for developers
- Site compatibility for Firefox 52
- Firefox Security Advisories
- Firefox Release Schedule