Chrome: The “HoeflerText” font wasn’t found scam
It is interesting from a purely scientific angle how attackers come up with new methods and schemes to distribute malicious payloads on to user systems.
The "HoeflerText" font wasn't found is a recent attack that changes website text so that it looks as if a font is missing, to get users to download and install an alleged update for Chrome that adds the font to the system.
I talked about this on the private Ghacks forum for supports back in January already. The first report about the attack came from Proofpoint to my best of knowledge.
The report reveals in detail how the attack works. Most of the technicalities behind the attack are probably not that interesting to the average Chrome user, so here is a short overview of the important tidbits:
- The attack requires that the user visits a compromised website.
- The attack script on the site checks various criteria -- country, user agent, and referrer -- and will only insert the font wasn't found script in the page if the criteria are met.
- If that is the case, the entire page is rewritten by the inserted script so that it looks garbled and becomes unreadable to the user.
- A popup is displayed afterwards to prompt the user to download the missing font and install it afterwards on the system. That download is the actual attack payload containing malicious code.
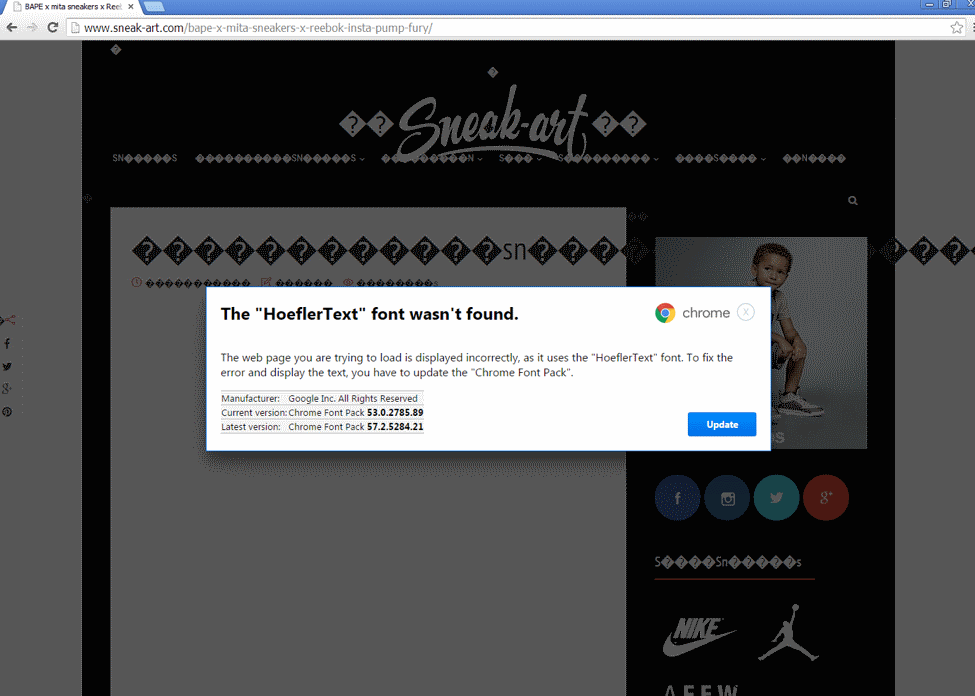
The popup is made to look as if it is an official prompt from the Chrome browser itself. It features a Google logo, and reads:
The "HoeflerText" font wasn't found.
The web page you are trying to load is displayed incorrectly, as it uses the "HoeflerText" font. To fix the error and display the text, you have to update the "Chrome Font Pack".
It displays (fake) manufacturer and Chrome Font Pack version information as well. A click on the update button downloads an executable file (Chrome_font.exe) to the system, and changes the popup to display information on how to run the executable file to update Chrome fonts.
Note: The prompts, name of the missing font that is used in the attack, and the file name may be changed at any time by attackers. It goes without saying that you should not click on the update button, nor install the downloaded executable file if you have done so.
What you can do
The only option you have is to wait until the site owner fixes the website to remove the malicious scripts running on it. Once done, it should go back to normal provided the cleaning was thorough.
If you need to access the site immediately, check out the The Wayback Machine to find out if an archived copy of it exists.