Microsoft Security Bulletins July 2016
Welcome to the Microsoft Security Bulletins overview for July 2016. The overview covers July's Patch Day, and all patches released by Microsoft on July 12, 2016 for Windows and other company products.
It starts with an executive summary that reveals important information about this month's security patches. It is followed by the operating system and Microsoft product distribution listing, revealing how specific Microsoft products are affected this month.
This is followed by the list of security bulletins released by Microsoft in July 2016, and the list of security advisories, updates, and non-security updates released since the June 2016 patch day.
The final part of the overview provides you with download information and links to additional resources.
Microsoft Security Bulletins July 2016
Executive Summary
- Microsoft released 11 bulletins on the July 2016 Patch Day.
- 6 bulletins are rated with a severity ranking of critical, the remaining 5 bulletins with a severity ranking of important.
- All client and server versions of Microsoft Windows are affected by security issues that the released patches resolve.
- Other affected Microsoft products include
Operating System Distribution
All client and server Windows operating systems are affected by at least one critical security vulnerability. In fact, all are affected by MS16-087, a vulnerability in Windows Print Spooler Components in a critical way.
Vista is the only client system affected by MS16-086, a cumulative security update for JScript and VBScript, and Windows Server 2008 the only server system affected by it but only with a moderate severity rating.
Windows 10 is the only client system affected by MS16-085, a cumulative security update for Microsoft Edge.
Windows 8.1 and newer systems are affected by MS16-093, another critically rated bulletin affecting Adobe Flash Player contained within IE10 and newer.
Last but not least, they receive updates described in MS16-092 and MS16-094. The updates fix secure boot and kernel security issues.
- Windows Vista: 3 critical, 2 important:
- Windows 7: 2 critical, 2 important
- Windows 8.1: 3 critical, 4 important
- Windows RT 8.1: 3 critical, 4 important
- Windows 10: 4 critical, 4 important
- Windows Server 2008: 1 critical, 2 important, 2 moderate
- Windows Server 2008 R2: 1 critical, 2 important, 1 moderate
- Windows Server 2012 and 2012 R2: 1 critical, 4 important, 2 moderate
- Server core: 1 critical, 4 important, 1 moderate
Other Microsoft Products
- Microsoft Office 2007, 2010, 2013, 2013 RT, 2016: 1 critical
- Microsoft Office for Mac 2011, 2016: 1 critical
- Microsoft Office Compatibility Pack Service Pack 3: 1 important
- Microsoft Excel Viewer: 1 important
- Microsoft Word Viewer: 1 important
- Microsoft SharePoint Server 2010, 2013, 2016: 1 important
- Microsoft Office Web Apps 2010, 2013: 1 important
- Office Online Server: 1 important
Security Bulletins
Cumulative Security Update for Internet Explorer (3169991) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer.
Cumulative Security Update for Microsoft Edge (3169999) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge.
Cumulative Security Update for JScript and VBScript (3169996) - Critical - Remote Code Execution
This security update resolves a vulnerability in the JScript and VBScript scripting engines in Microsoft Windows. The vulnerability could allow remote code execution if a user visits a specially crafted website. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.
Security Update for Windows Print Spooler Components (3170005) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if an attacker is able to execute a man-in-the-middle (MiTM) attack on a workstation or print server, or set up a rogue print server on a target network.
Security Update for Microsoft Office (3170008) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user.
Security Update for Windows Secure Kernel Mode (3170050) - Important - Information Disclosure
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure when Windows Secure Kernel Mode improperly handles objects in memory.
Security Update for Windows Kernel-Mode Drivers (3171481) - Important - Elevation of Privilege
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system.
Security Update for .NET Framework (3170048) - Important - Information Disclosure
This security update resolves a vulnerability in Microsoft .NET Framework. The vulnerability could cause information disclosure if an attacker uploads a specially crafted XML file to a web-based application.
Security Update for Windows Kernel (3171910) - Important - Security Feature Bypass
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow security feature bypass if the Windows kernel fails to determine how a low integrity application can use certain object manager features.
Security Update for Adobe Flash Player (3174060) - Critical - Remote Code Execution
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows RT 8.1, Windows Server 2012 R2, and Windows 10.
Security Update for Secure Boot (3177404) - Important - Security Feature Bypass
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow Secure Boot security features to be bypassed if an attacker installs an affected policy on a target device. An attacker must have either administrative privileges or physical access to install a policy and bypass Secure Boot.
Security advisories and updates
MS16-083: Security Update for Adobe Flash Player for Windows 10, Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows Embedded 8 Standard, and Windows Server 2012 (KB3167685)
Non-security related updates
KB2952664: Update for Windows 7 - Compatibility update for upgrading Windows 7.
KB2976978: Update for Windows 8.1 and Windows 8 - Compatibility update for Windows 8.1 and Windows 8.
KB2977759: Update for Windows 7 - Compatibility update for Windows 7 RTM.
KB3170735: Update for Windows 8.1 and Windows 7 - July 2016 Update for Windows Journal.
KB3163589: Update for Windows 8 and Windows 7 - "Your PC is running an outdated version of Windows" notification.
KB3173040: Update for Windows 8.1 and Windows 7 - Windows 8.1 and Windows 7 SP1 end of free upgrade offer notification.
KB3161606: Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 - June 2016 update rollup for Windows RT 8.1, Windows 8.1, and Windows Server 2012 R2
Issues that the update fixes:
- KB3163232 Application crashes when you open an earlier version of an Office file in Windows 8.1 or Windows Server 2012 R2
- KB3163974 "Sign in to your Microsoft account" wizard page has only one text box in Windows 8.1 or Windows Server 2012 R2
- KB3142535 Hard I/O failure with MPIO storage targets connected to Windows Server 2012 R2
- KB3153887 Fine tuning failover cluster network thresholds in Windows Server 2012 R2
- KB3163306 AD FS 3.0 can't connect to native LDAP attribute stores over SSL in Windows Server 2012 R2
- KB3163192 NFS role takes a long time or fails to come online on a Windows Server 2012 R2 cluster
- KB3164088 Memory leak occurs when system calls a certain function to store and look for GUID records in Windows Server 2012 R2
- KB3164345 Stop error occurs when you recover a computer from sleep or restart it in Windows 8.1 or Windows RT 8.1
- KB3135021 File server becomes unresponsive when data deduplication is running in Windows Server 2012 R2
- KB3159393 Memory Leak in IIS ADSI provider in Windows 8.1 or Windows Server 2012 R2
- KB3159985 Crash dump file isn't generated in Windows Server 2012 R2
- KB3162159 Kerberos authentication policy causes requests to fail with a status of KDC_ERR_POLICY in Windows Server 2012 R2
- KB3162871 RD Gateway Manager console crashes with the latest .NET Framework 4.6.1 update on Windows Server 2012 R2
- KB3163023 Windows Update Client for Windows 8.1 and Windows Server 2012 R2: June 2016
- KB3161579 "Access Denied" error when you run mpclaim.exe command to retrieve MPIO configuration reports in Windows Server 2012 R2
- KB3154769 "Error Cannot Process TPM Attestation" when you try to configure Key Attestation in Windows Server 2012 R2
- KB3163191 Group policies aren't applied during startup and logon in Windows
- KB3154437 Update to remove VPNIKE hardcoded dependency in Windows Server 2012 R2
- KB3153727 Windows Installer with certain actions can't be installed on Windows Server 2012 R2 or Windows Server 2008 R2 SP1
- KB3161639 Update to add new cipher suites to Internet Explorer and Microsoft Edge in Windows
- KB3158626 "0xD1" Stop error when a virtual machine crashes on a Windows Server 2012 R2 or Windows Server 2012 Hyper-V host
- KB3154228 32-bit icons can't be loaded in OleLoadPictureEx in Windows
KB3161608: Update for Windows 7 and Windows Server 2008 R2 - June 2016 update rollup for Windows 7 SP1 and Windows Server 2008 R2 SP1
Issues that the update fixes:
- KB3154228 32-bit icons can't be loaded in OleLoadPictureEx in Windows
- KB3153727 Windows Installer with certain actions can't be installed on Windows Server 2012 R2 or Windows Server 2008 R2 SP1
- KB3161647 Windows Update Client for Windows 7 and Windows Server 2008 R2: June 2016
- KB3161897 WDS deployment fails when UEFI clients are in routed environments in Windows Server 2008 R2 SP1
- KB3161639 Update to add new cipher suites to Internet Explorer and Microsoft Edge in Windows
- KB3163644 Microsoft Office 2010 doesn't start when EMET is enabled in Windows 7 or Windows Server 2008 R2
KB3161609: Update for Windows Embedded 8 Standard and Windows Server 2012 - June 2016 update rollup for Windows Server 2012
Issues that the update fixes:
- KB3158626 "0xD1" Stop error when a virtual machine crashes on a Windows Server 2012 R2 or Windows Server 2012 Hyper-V host
- KB3154228 32-bit icons can't be loaded in OleLoadPictureEx in Windows
How to download and install the July 2016 security updates
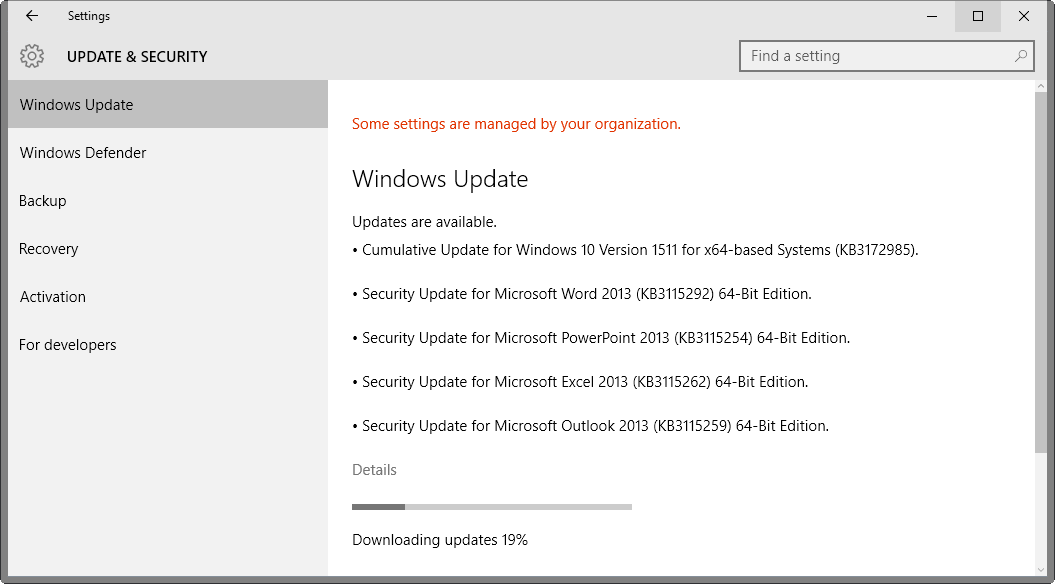
All security updates are already available on Windows Update. Windows Update is the built-in update service of Windows devices, and configured by default to download critical patches automatically.
The service does not check for updates in real-time. If you want to speed up the process, do the following:
- Tap on the Windows-key on the computer keyboard, type Windows Update, and select the result from the list.
- Select the "check for updates" button to run a manual check for updates.
Windows checks for available updates. What happens next depends on how updating is configured on the device. Updates may be downloaded and installed automatically, or you may be notified about them only.
The latter gives you greater control over the updating process.
We recommend highly that you research updates released for Windows before you install them on your machines. Updates may break systems, and have done so in the past. At the very least, create a system backup before you install the updates.
Some updates are available on Microsoft's Download Center, as Security ISO images, and via Microsoft's Update Catalog.
Additional resources