OEM Updaters put PCs at risk
A study by Duo Security, Inc suggests that OEM Updaters, programs designed by PC manufacturers to update vendor-specific software, do more harm than good as they put PCs at risk.
Prebuild desktop computers, laptops and tablets ship with a set of added applications and programs more often than not. Commonly referred to as crapware, these programs add little value to the system and are often comprised of trial versions, shortcuts, and programs created by the manufacturer of the device.
Manufactures add these in part to make money but also to push their software applications on the devices.
The past has shown that the added content may not only be a nuisance to users but also put the computer at risk.
Duo Security's analysis of update programs by OEMs hammers that point home further. The company concluded that every updater that it analyzed had at least one vulnerability that allowed remote code execution to completely compromise the machine.
The company looked at devices from Acer, Asus, Dell, Hewlett-Packard and Lenovo and found a total of 12 vulnerabilities across all update programs. It looked primarily at man in the middle attacks and remote attack surfaces.
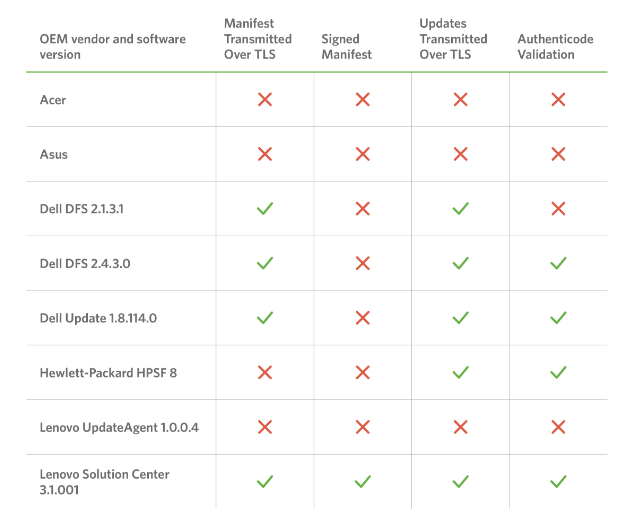
via Duo.com
The core issues found were the following ones:
- All devices shipped at least with one preinstalled updater that is vulnerable to attacks.
- These programs often failed to make use of TLS, update integrity validations, or authenticity validations of update manifest contents.
- Some vendors make use of multiple programs to update software, with some often being more secure than others.
- Exploiting the vulnerabilities is trivial according to the researchers.
All vendors, with the exception of Dell, transferred manifest files over HTTP. Furthermore Acer and Asus don't transfer files over HTTPS at all while Dell and HP did. Lenovo was the only company in the test that had one program use no HTTPS connections at all, and another that supported HTTPS and used it.
Not using HTTPS for transfers is bad practice for obvious reasons. Since most manufacturers use HTTP when transferring manifest files -- used to inform the system of updates -- it is easy enough for attackers to manipulate those files. This in turn makes integrity checks useless as it is impossible to verify the integrity of files or updates if the authenticity of the manifest file cannot be verified.
The full research paper, Out-of-Box Exploitation of OEM Updaters, is available here.
Mitigation of issues
The main issue for users is that there is little that they can do to mitigate the issues found in these update programs short of removing these (and other vendor components) from the device.
Here are a couple of suggestions:
- Create a full system backup.
- Uninstall software programs that shipped with the PC that were added by the manufacturer of the device unless you know that you require it.
- Most of the time, those are not needed to operate the system. Programs like Decrap or Decrapifier may help somewhat, but they usually don't remove vendor software.
If you are about to buy a PC and don't want to build it yourself, try grabbing a Microsoft Signature Edition which ship without bloatware.
Closing Words
Security issues caused by manufacturers of PCs, laptops and other computing devices are a recurring scheme, and it seems unlikely that the situation will get better in the near future.
Now You: Is vendor-specific software still running on your devices?