Secure you wireless router
There is no such thing as perfect security. Given enough knowledge, resources, and time any system can be compromised. The best you can do is to make it as difficult for an attacker as possible. That said there are steps you can take to harden your network against the vast majority of attacks.
The default configurations for what I call consumer-grade routers offer fairly basic security. To be honest, it doesn’t take much to compromise them. When I install a new router (or reset an existing), I rarely use the ‘setup wizards’. I go through and configure everything exactly how I want it. Unless there is a good reason, I usually don’t leave it as default.
I cannot tell you the exact settings you need to change. Every router’s admin page is different; even router from the same manufacturer. Depending on the specific router, there may be settings you can’t change. For many of these settings, you will need to access the advanced configuration section of the admin page.
I’ve included screenshots of an Asus RT-AC66U. It is in the default state.
Update your firmware. Most people update the firmware when they first install the router and then leave it alone. Recent research has shown that 80% of the 25 top-selling wireless router models have security vulnerabilities. Affected manufacturers include: Linksys, Asus, Belkin, Netgear, TP-Link, D-Link, Trendnet, and others. Most manufacturers release updated firmware when vulnerabilities are brought to light. Set a reminder in Outlook or whatever email system you use. I recommend checking for updates every 3 months. I know this sounds like a no-brainer, but only install firmware from the manufacturer’s website.
Also, disable the router’s capability to automatically check for updates. I’m not a fan of letting devices ‘phone home’. You have no control over what date is sent. For example, did you know that several so-called ‘Smart TVs’ send information back to their manufacturer? They send all your viewing habits every time you change the channel. If you plug a USB drive into them, they send a list of every filename on the drive. This data is unencrypted and is sent even if the menu setting is set to NO.
Disable remote administration. I understand some people need to be able to reconfigure their network remotely. If you have to, at least enable https access and change the default port. Note that this includes any type of ‘cloud’ based management, such as Linksys’ Smart WiFi Account and Asus’ AiCloud.
Use a strong password for router admin. Enough said.
Enable HTTPS for all admin connections. This is disabled by default on many routers.
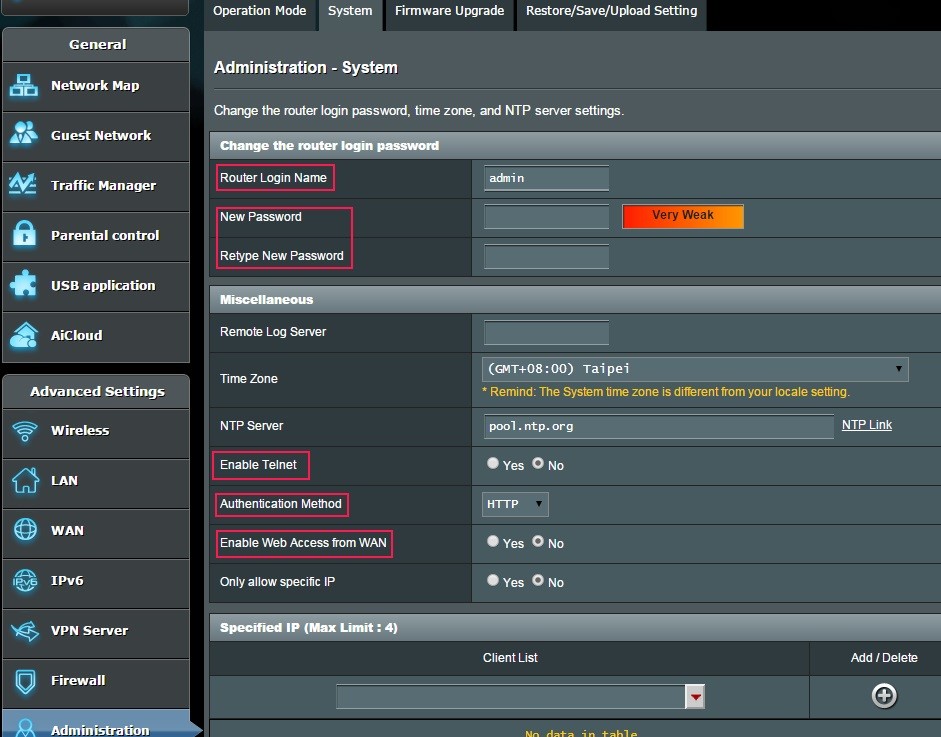
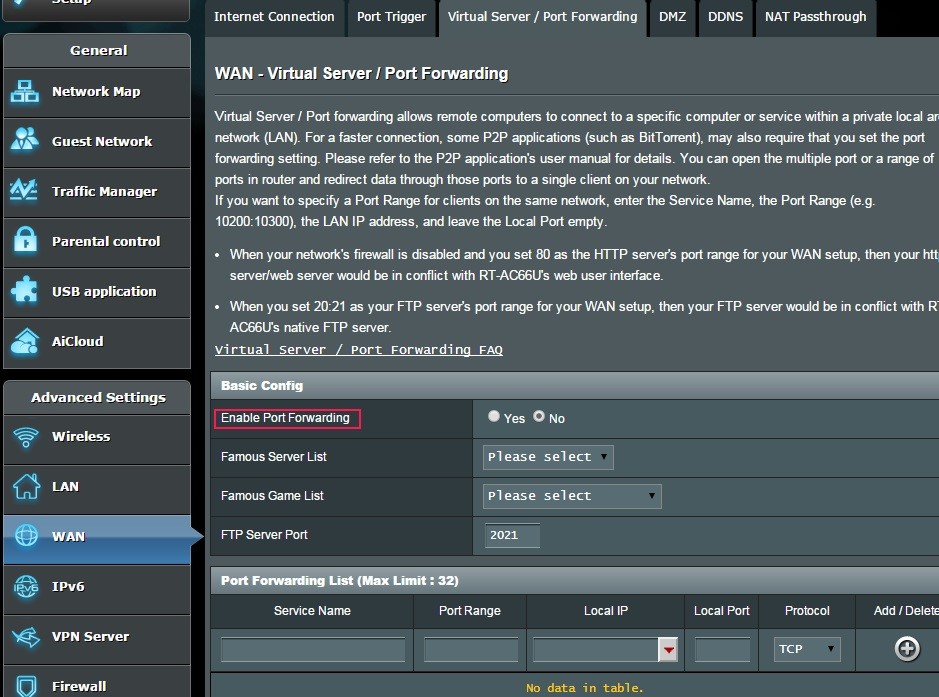
Restrict inbound traffic. I know this is common sense, but sometimes people don’t understand the consequences of certain settings. If you must use port forwarding, be very selective. If possible, use a non-standard port for the service you’re configuring. There are also settings for filtering anonymous internet traffic (yes), and for ping response (no).
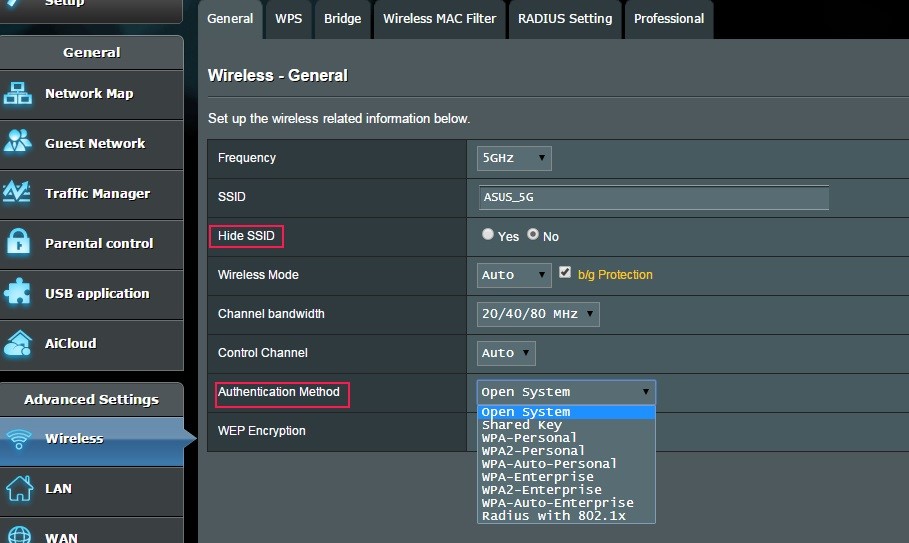
Use WPA2 encryption for the WiFi. Never use WEP. It can be broken within minutes with software freely available on the internet. WPA isn’t much better.
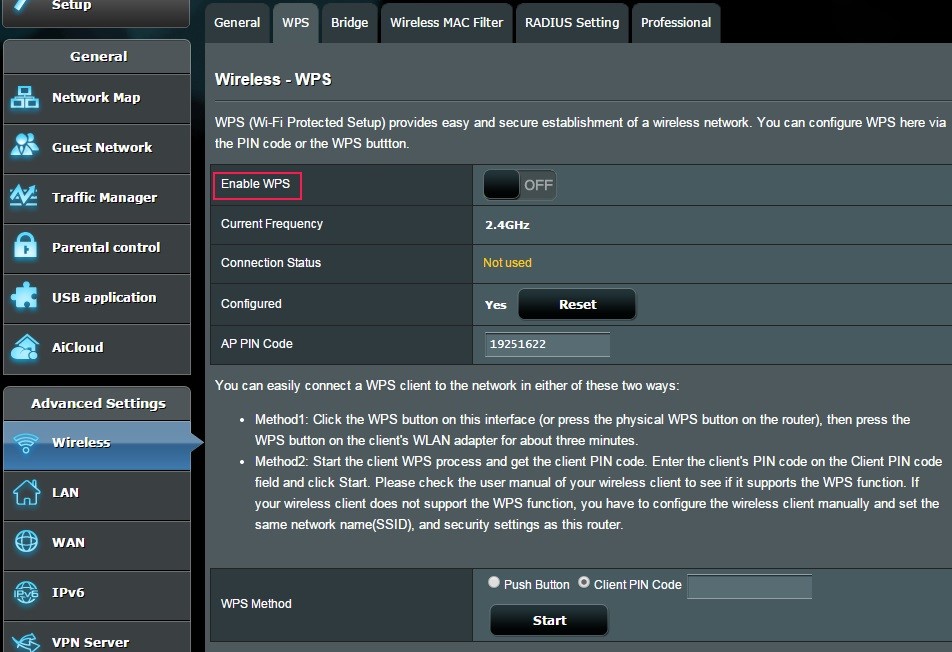
Turn off WPS (WiFi Protected Setup). I understand the convenience of using WPS, but it was a bad idea to start.
Restrict outbound traffic. As mentioned above, I normally don’t like devices that phone home. If you have these types of devices, consider blocking all internet traffic from them.
Disable unused network services, especially uPnP. There is a widely known vulnerability when using uPnP service. Other services probably unnecessary: Telnet, FTP, SMB (Samba/file sharing), TFTP, IPv6
Log out from the admin page when done. Just closing the web page without logging out can leave an authenticated session open in the router.
Check for port 32764 vulnerability. To my knowledge some routers produced by Linksys (Cisco), Netgear, and Diamond are affected, but there may be others. Newer firmware was released, but may not fully patch the system.
Check your router at: https://www.grc.com/x/portprobe=32764
Turn on logging. Look for suspicious activity in your logs on a regular basis. Most routers have the capability of emailing the logs to you at set intervals. Also make sure the clock and time zone are set correctly so that your logs are accurate.
For the truly security-conscious (or maybe just paranoid), the following are additional steps to consider
Change the admin user name. Everyone knows the default is usually admin.
Set up a ‘Guest’ network. Many newer routers are capable of creating separate wireless guest networks. Ensure it only has access to the internet, and not your LAN (intranet). Of course, use the same encryption method (WPA2-Personal) with a different passphrase.
Do not connect USB storage to your router. This automatically enables many services on your router and may expose the contents of that drive to the internet.
Use an alternate DNS provider. Chances are you are using whatever DNS settings your ISP gave you. DNS has increasingly become a target for attacks. There are DNS providers who have taken additional steps to secure their servers. As an added bonus, another DNS provider may increase your internet performance.
Change the default IP address range on your LAN (inside) network. Every consumer-grade router I’ve seen uses either 192.168.1.x or 192.168.0.x making it easier to script an automated attack.
Available ranges are:
Any 10.x.x.x
Any 192.168.x.x
172.16.x.x to 172.31.x.x
Change the router’s default LAN address. If someone does gain access to your LAN, they know the router’s IP address is either x.x.x.1 or x.x.x.254; don’t make it easy for them.
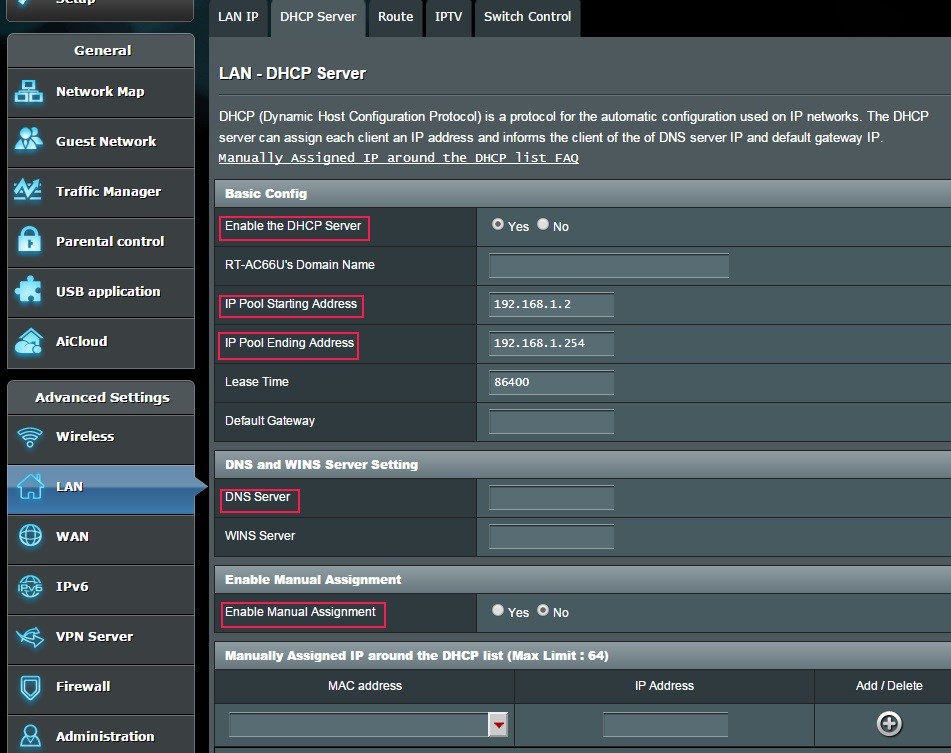
Disable or restrict DHCP. Turning off DHCP is usually not practical unless you’re in a very static network environment. I prefer to restrict DHCP to 10-20 IP addresses starting at x.x.x.101; this makes it easier to keep track of what’s happening on your network. I prefer to put my ‘permanent’ devices (desktops, printers, NAS, etc.) on static IP addresses. That way only laptops, tablets, phones, and guests are using DHCP.
Disable admin access from wireless. This functionality is not available on all home routers.
Disable SSID broadcast. This is not difficult for a professional to overcome and can make it a pain to allow visitors on your WiFi network.
Use MAC filtering. Same as above; inconvenient for visitors.
Some of these items fall into the category of ‘Security by Obscurity’, and there are many IT and security professionals that scoff at them, saying they are not security measures. In a way, they are absolutely correct. However, if there are steps you can take to make it more difficult to compromise your network, I think it’s worth considering.
Good security is not ‘set it and forget it’. We’ve all heard about the many security breaches at some of the biggest companies. To me, the really irritating part is when you here they had been compromised for 3, 6, 12 months or more before it was discovered.
Take the time to look through your logs. Scan your network looking for unexpected devices and connections. If you want a quick and easy way to see what’s on your network, Fing is a handy app, available for IOS, Android, Windows, Mac,etc. http://www.overlooksoft.com/fing
Below are some authoritative references:
- NSA - https://www.nsa.gov/ia/_files/factsheets/I43V_Slick_Sheets/Slicksheet_BestPracticesForKeepingYourHomeNetworkSecure.pdf
- US-CERT - https://www.us-cert.gov/sites/default/files/publications/HomeRouterSecurity2011.pdf